Phishing danger in MS Teams: vulnerability to bypass link restrictions

Share the blog with others
Vulnerability in Microsoft Teams: Hidden Phishing Risks in Current Attack Waves
Microsoft Teams has become an indispensable tool for corporate communication. However, this popularity and the trust that many users place in Teams have also made it interesting for attackers. Several months ago, we discovered a security flaw in Microsoft Teams that allowed phishing links to be embedded in team descriptions. This vulnerability, which arose due to insufficient input validation, could be exploited by attackers to send malicious links via Microsoft invitations, thereby deliberately exploiting users' trust.
Overview of the Vulnerability: Input Validation in Microsoft Teams
In Microsoft Teams, users were not allowed by default to insert URLs into the description of a team to minimize phishing risks. However, this restriction was implemented only on the frontend side – that is, the user interface. Attackers were able to bypass the check by submitting the form quickly or using network tools like Burp Suite to modify the team description text and send it directly to the backend.
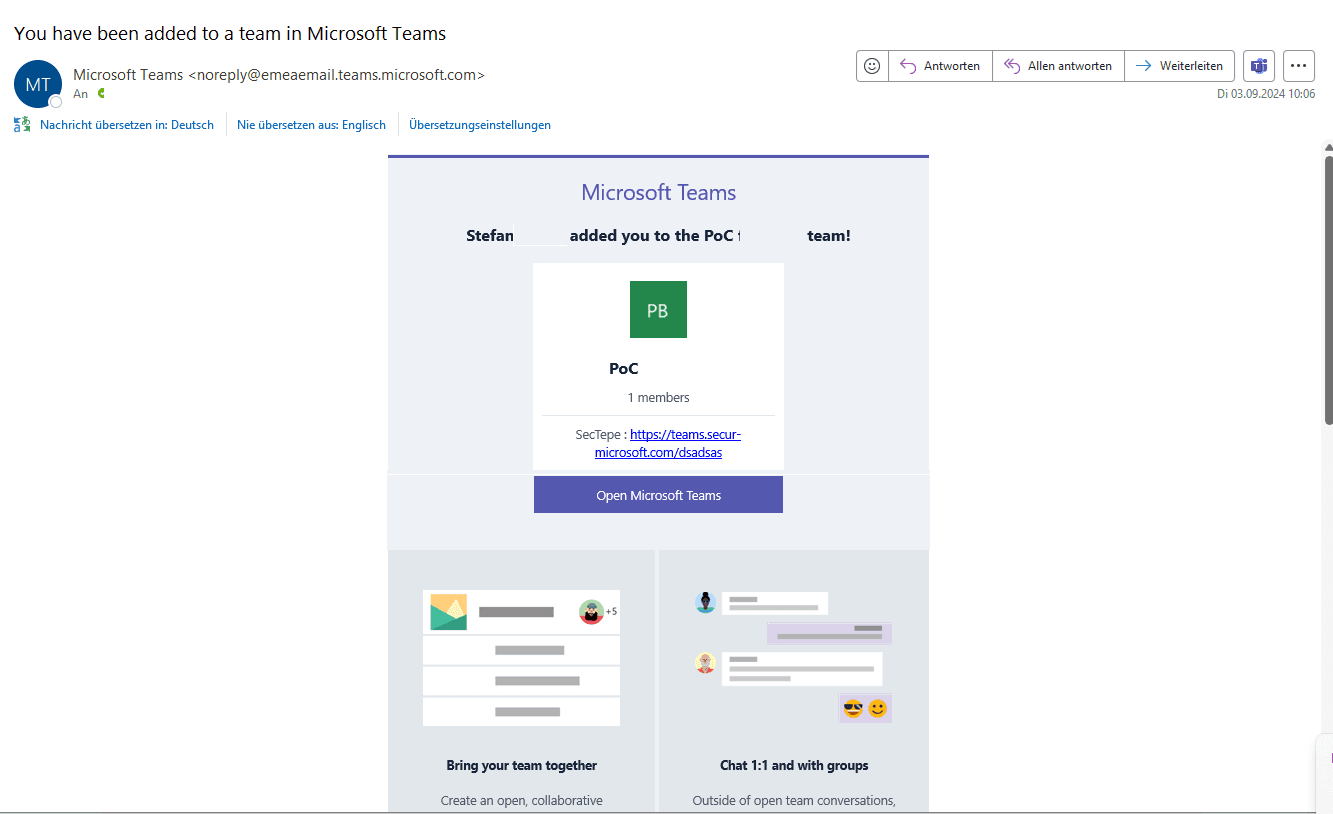
Once the team was created with the URL, this description was sent with each invitation link to new members – through an official Microsoft domain. This made the invitation appear legitimate, and recipients were more likely to click on the embedded link.
Quick Form Submission: Submitting the form quickly with a click before the validation is fully completed.
Network Interception Tools: Using tools like Burp Suite or the browser's developer tools to intercept the request and modify the description text to pass the URL directly to the backend.
When a team was created with such a manipulated description, the malicious link was included in all invitations sent to new members. Since the email was sent from a trusted Microsoft domain, it is very likely that recipients viewed the message as legitimate and clicked on the link. This significantly increased the risk of a successful phishing attack.
Step-by-Step Guide to Reproduce
The following are the exact steps to reproduce the vulnerability and illustrate the danger it poses:
Log in and Create a Team: Sign in to Microsoft Teams and create a new team.
Insert Link in the Description: Enter a URL in the "Description" field. Normally, Microsoft Teams blocks this with an error message.
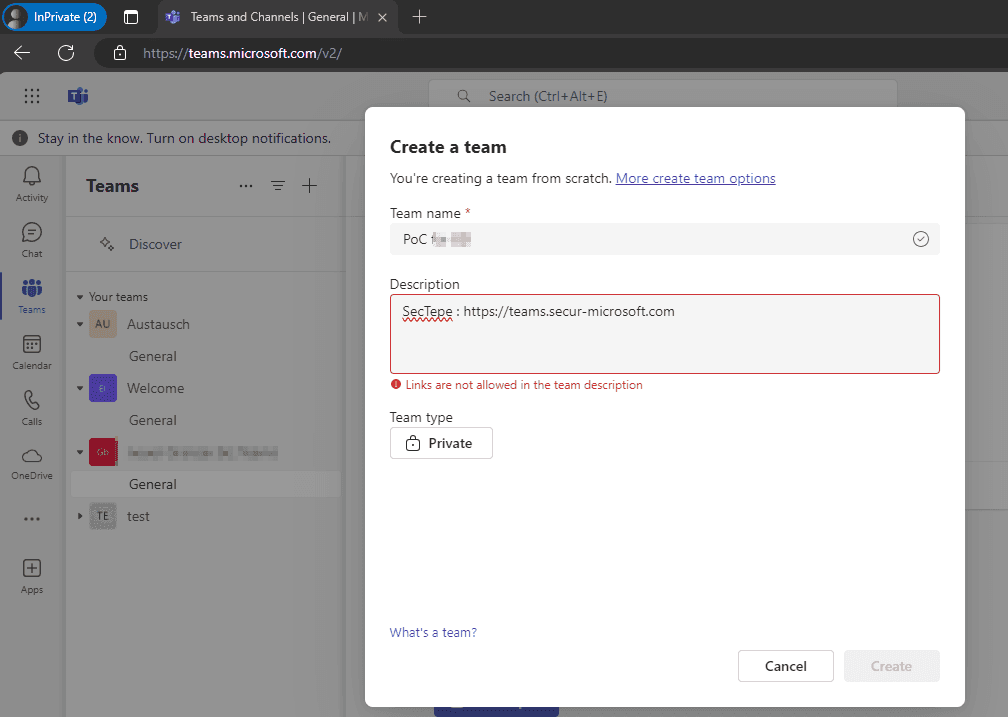
Bypass Frontend Validation: Use one of the following methods:
Click on “Create” before the frontend validation has fully checked the input.
Alternatively, you can use a network tool to intercept the request and modify the description before forwarding it to the backend.
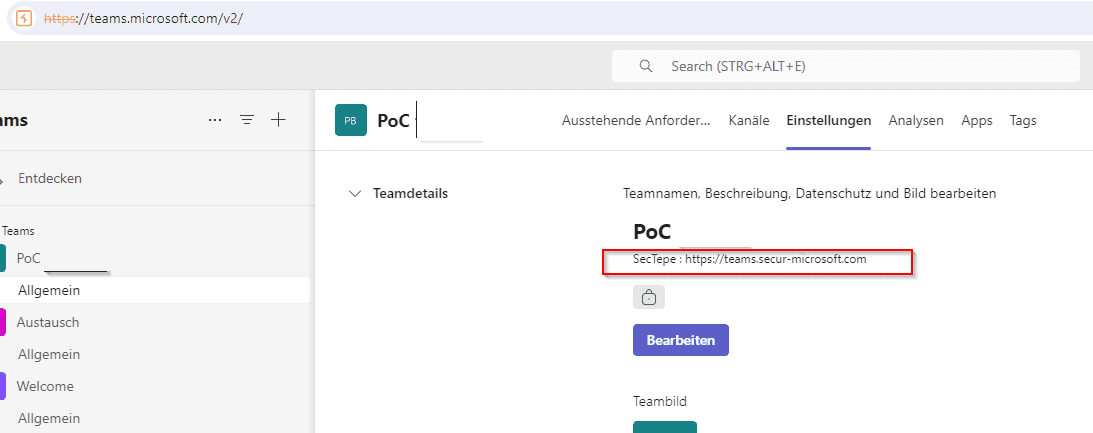
Invite Members: Add new members to the team who will receive an invitation email with the manipulated description.
Check Email: Open the email received by the new members. This email contains the malicious link embedded in the team description and sent through the trusted Microsoft domain.
Guest Invitation:
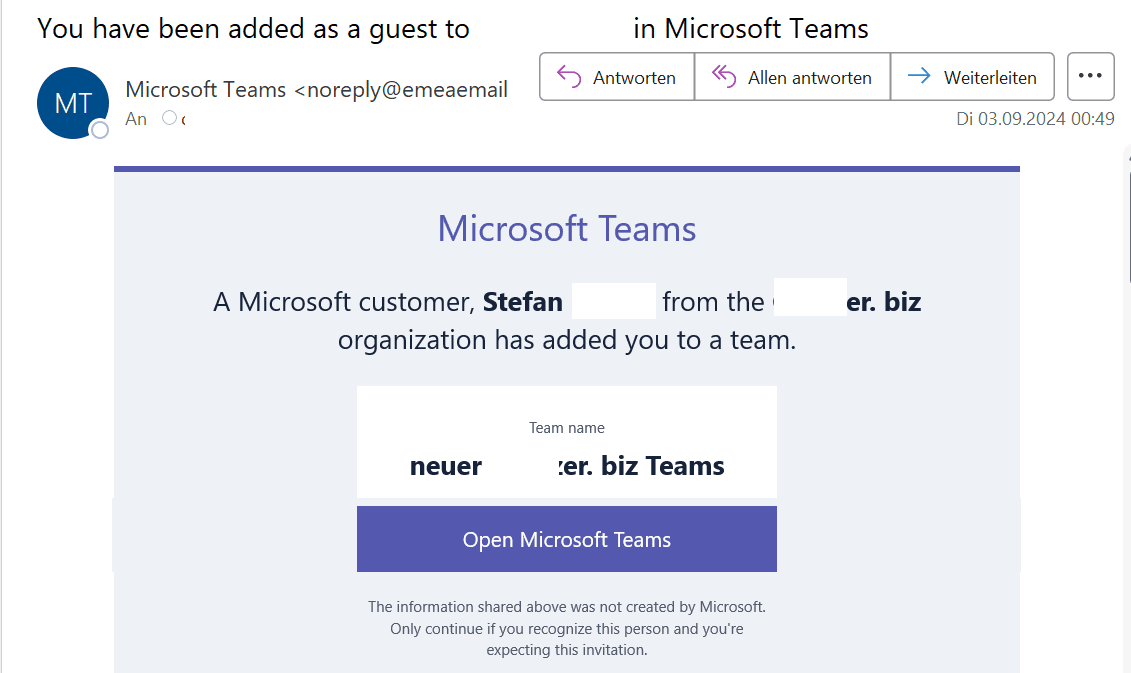
Invitation in the Teams with possible malicious link:
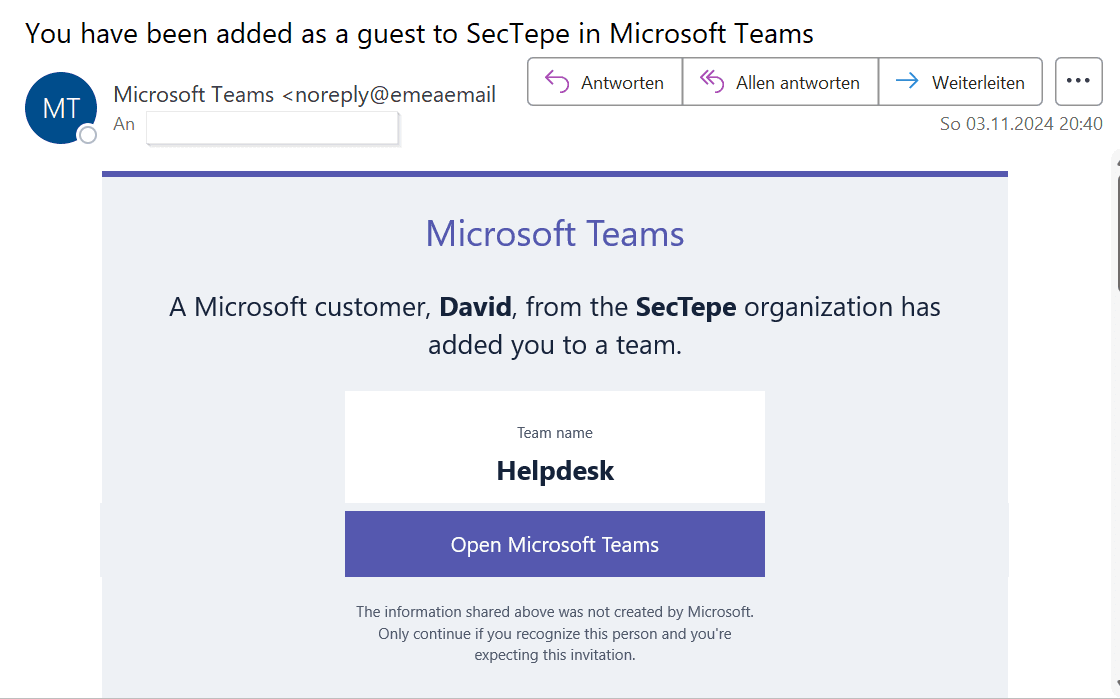
As of November 3, 2024, Microsoft has removed the description from the email invitations.
Practical Dangers: Phishing Attacks and Current Media Reports
This vulnerability posed a significant risk as attackers could distribute malicious links via a familiar platform like Microsoft Teams. Numerous media outlets recently reported on hackers using Teams to impersonate IT support or other trusted senders. A recent article in Forbes describes how attackers are specifically abusing Teams for ransomware and phishing attacks.
Our own security assessments have shown that this method is effective: In simulated phishing tests via Teams, we achieved a success rate of 20%. Particularly concerning is that the vulnerability allowed attackers to place links in the very first invitation, significantly increasing the risk for unsuspecting recipients.
Microsoft Responds: Vulnerability Fixed
After we responsibly reported the security flaw, Microsoft initially classified it as less urgent and added it to the backlog. However, following the release of the bug and increasing media coverage of similar attacks, Microsoft has now responded and resolved the vulnerability. With a patch, the team description has been removed from invitation emails. This means that newly added team members no longer see the description – and potentially harmful links – in their invitations. This significantly reduces the likelihood of a successful phishing attack via Teams invitations.
The CVSS Score and the Underestimated Danger
One reason Microsoft initially prioritized the vulnerability as low was due to the CVSS score, which was rated as "Medium" because of the required user interaction. However, the actual risk was higher, as Teams is a trusted platform for many users, and recipients are more likely to click on embedded links without suspicion. The swift implementation of the patch demonstrates that the real context – and not just the technical score – should be considered in security assessments.
Conclusion and Recommendations
The vulnerability in Microsoft Teams shows that a "Medium" score in the CVSS system can underestimate the actual dangers to users in practice. While the input validation on the platform gives a false sense of security, attackers are able to bypass this measure and embed phishing links in Microsoft Teams invitations. Combined with the trust that users have in invitations from Microsoft Teams, this vulnerability can serve as an effective method for phishing attacks and cause serious harm.
Recommendations for Users and Companies:
Vigilance with Teams Invitations: Raise awareness among your employees about the risks of unexpected invitations and emphasize that even trusted platforms like Microsoft Teams can be abused.
Training and Awareness Programs: Regularly train your teams in phishing detection and response to suspicious messages – even on seemingly trusted platforms.
Security Audits and Testing: Consider regular phishing simulations to improve your employees' awareness and adapt your security strategy to current threats.
Make your company secure from phishing attacks via Microsoft Teams and other platforms. Our security experts can help you identify vulnerabilities and prepare your employees for such threats. Contact us for personalized security consulting and strengthen your defenses against modern cyber attacks!
Timeline:
September 18, 2024 - Report to Microsoft
October 9, 2024 - Microsoft does not classify the vulnerability as Important or Critical; the bug is added to the backlog and the ticket is closed
November 20, 2024 - November 3, 2024 Microsoft patches the vulnerability without notification
November 3, 2024 - Disclosure of the vulnerability by SecTepe